PCI DSS Compliance: Audit Requirements, Risks, and Controls
The Payment Card Industry Data Security Standard (PCI DSS) version 4.0 establishes comprehensive requirements for organizations that handle cardholder data. This guide outlines the key audit requirements, associated risks, and essential controls needed for compliance.
1. Network Security Requirements
Key Controls:
- Installation and maintenance of network firewalls
- Secure configuration standards for all system components
- Network segmentation validation
- Regular network security testing and monitoring
Associated Risks:
- Unauthorized access to cardholder data environment
- Network security breaches
- Data leakage through misconfigured systems
2. Cardholder Data Protection
Key Controls:
- Encryption of stored cardholder data
- Secure transmission of cardholder data across networks
- Access control mechanisms
- Data retention and disposal procedures
Associated Risks:
- Data breaches during transmission
- Unauthorized data storage
- Improper data disposal
3. Access Control Measures
Required Controls:
- Role-based access control implementation
- Unique ID assignment for system access
- Multi-factor authentication for remote access
- Regular access rights review and validation
Associated Risks:
- Unauthorized system access
- Privilege escalation
- Compromised user credentials
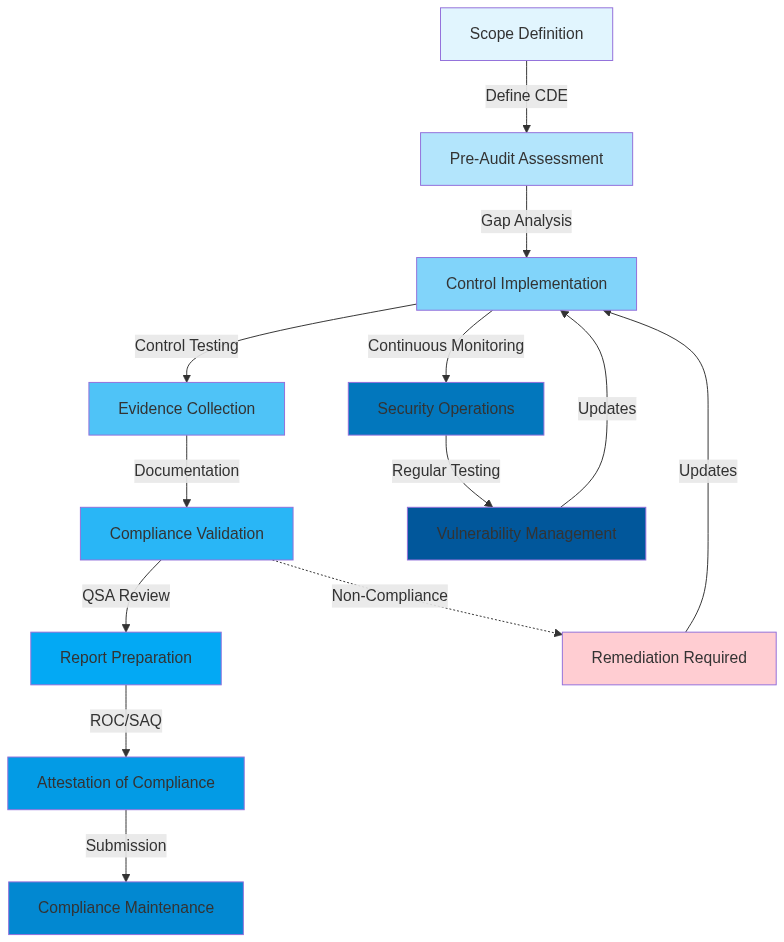](https://mermaid-js.github.io/mermaid-live-editor/edit#pako:eNp9lMFymzAURX9Fo25tF2xjA4vOEOM4TsZNY6dZFGch4MnRjJAoiLSuyb9XFsTRdFFWiHPv09WT0AlnMgcc4kNFyhf0GO8F0k-U7DJZAoqBMsEUk-IZDYdfWjMGtIiXLbpKvlUwjJqcKRTVNdR1AUI9dwWujHxFShQJwo81q1u0SBZSqEpytC5KDmc1MaU7y8JY3iWPUCsmDi2Kk-Ury0FkelrJOWSWJe5Cyay5FGvRUk-j6zNytjwRznJ7lqWxPOwitIVXBr9adJ1soZSVQno5Jals8bURb-8Xn3fRQ4tWSaSUzmUkSFL0MVFvWBnDrkkLVtcmzY2dZkOYUCAsw79LZ6KRTY02UnddVqYB62QHWVMxdUT3JXT56t6-7gLCoeGk-ujZbfLUcKG1KeNn34YIcgBre26N73upWwPnnbHD6A6NNPwqxfAjeovudJsKyFm3-C38bFgFeV_v7j_1anXkgCJEGefhJ3CpR8EmVz1JJ-DRzCaLnvhuPqXEJnFPpjSb0LlNlj0ZB-mMzmxy3RNnQgI6tcnqQoIUPJvcvJOx7-euTdYXMp-nuU1u34nrzYPUJnc9oTTL8zEe4AKqgrBc_36ns26P1Yvu8R6H-jUHShqu9ngv3rSUNErujiLDISW8hgGuZHN4uYwa0_qYEf0fF5evJRE_pNRjVTXdEIcn_BuHk2Dk-q7jzqb-3J86vjfARxwOnZGO7Hue4wS-7zvudPw2wH9MBWcUOMHMDfzZxAt8Zz4eYH0Y9BnddPeHuUbe_gIJjF_J))
4. Vulnerability Management
Required Controls:
- Regular vulnerability scanning
- Timely patch management
- Secure system and application development
- Change management procedures
Associated Risks:
- System vulnerabilities exploitation
- Application security breaches
- Insecure code deployment
5. Security Testing and Monitoring
Required Controls:
- File integrity monitoring
- Security event logging and monitoring
- Intrusion detection/prevention systems
- Regular penetration testing
Associated Risks:
- Undetected security incidents
- Delayed incident response
- System compromise
6. Security Policy and Procedures
Required Controls:
- Information security policy documentation
- Security awareness training
- Incident response procedures
- Business continuity planning
Associated Risks:
- Policy non-compliance
- Inadequate security awareness
- Ineffective incident response
7. Third-Party Risk Management
Required Controls:
- Service provider compliance monitoring
- Written agreements with security requirements
- Regular service provider assessments
- Third-party access management
Associated Risks:
- Third-party security breaches
- Data exposure through service providers
- Contractual non-compliance
