Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

Understanding GRC Audit: A Strategic Approach to Governance, Risk, and Compliance Assessment GRC (Governance, Risk, and Compliance) audit represents a comprehensive assessment methodology that evaluates an organization’s governance structures, risk management processes, and compliance posture within a unified framework. Unlike…

Cybersecurity as a Service (CaaS) in NCA SOC Framework Saudi Arabia’s National Cybersecurity Authority (NCA) has transformed the cybersecurity landscape through its comprehensive SOC (Security Operations Center) licensing framework and the emerging Cybersecurity as a Service (CaaS) model. As organizations…

Responding to Incidents: Tabletop Exercises for Crisis Management In today’s rapidly evolving threat landscape, effective incident response requires more than documented procedures—it demands practiced coordination, tested communication channels, and refined decision-making capabilities. Tabletop exercises represent the cornerstone of modern crisis…

Preparing for Cyber Resilience: Strengthening Business Continuity Management Preparing for Cyber Resilience: Strengthening Business Continuity Management As Saudi Arabia advances its ambitious Vision 2030 digital transformation agenda, organizations face an unprecedented convergence of cyber threats and operational disruptions. With massive…

NCA ECC: Benefits and Implementation Steps for Healthcare Companies in Saudi Arabia Healthcare organizations in Saudi Arabia face unprecedented cybersecurity challenges while managing sensitive patient data. The National Cybersecurity Authority’s Essential Cybersecurity Controls (NCA ECC) framework provides a structured approach…
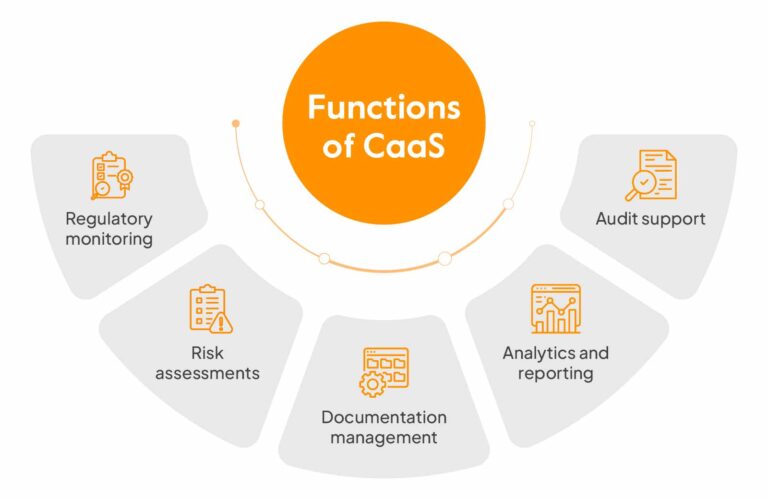
Compliance as a Service: Transforming Business Operations Under NCA and SAMA Requirements As Saudi Arabia accelerates its digital transformation under Vision 2030, organizations face increasingly complex regulatory compliance requirements from the National Cybersecurity Authority (NCA) and Saudi Arabian Monetary Authority…
Comprehensive Guide to GRC Systems in Financial Institutions The integration of Governance, Risk, and Compliance (GRC) systems in financial institutions represents a fundamental shift in how organizations manage their regulatory obligations, risk exposure, and governance frameworks. This comprehensive guide explores…
Cybersecurity Disaster Recovery Scenarios: Implementation Guide This comprehensive implementation guide provides detailed technical steps and considerations for developing and executing disaster recovery scenarios. Each scenario includes specific technical requirements, implementation steps, and validation procedures. 1. Ransomware Attack Implementation Scenario Parameters…

Physical Security in Data Centers: A Comprehensive Guide Perimeter Security Building Security Floor Security Room Security Rack Security • Fencing • Guards • CCTV • Access Control • Mantraps • Biometrics • Card Readers • Monitoring • Environmental • Fire…

Traditional Bank Open Banking APIs Account Information Payment Initiation Product Information Consent Management FinTech Apps Consumers Open Banking represents a paradigm shift in how financial institutions operate and deliver services to customers. Through standardized APIs, banks are now enabling secure…